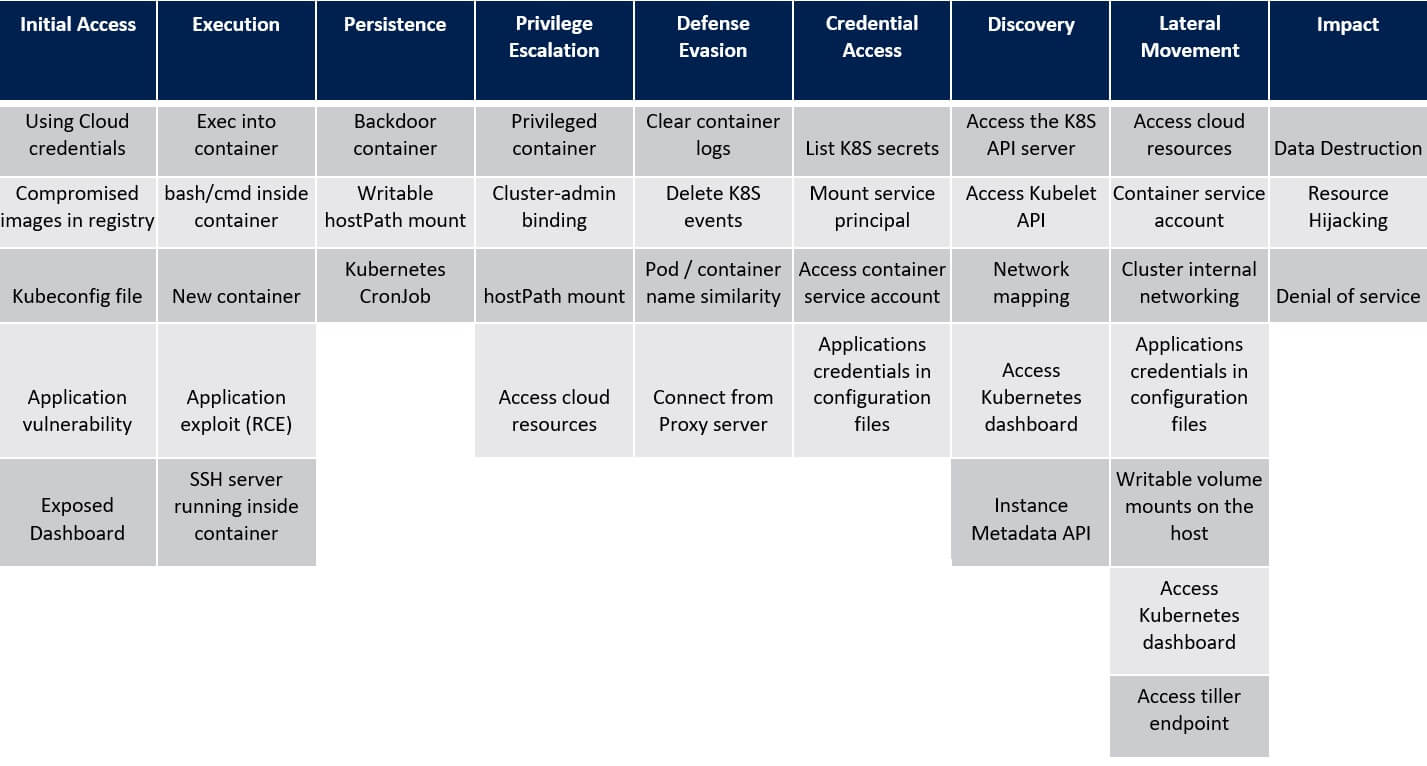
7. Discovery in the Kubernetes Cluster – ATT&CK® Matrix
MITRE’s ATT&CK®
Access the Kubernetes API server
The Kubernetes API server is the gateway to the cluster. Actions in the cluster are performed by sending various requests to the RESTful API. The status of the cluster, which includes all the components that are deployed on it, can be retrieved by the API server. Critics may send API requests to probe the cluster and fetch information about containers, secrets, and additional resources in the cluster.
Access Kubelet API
Kubelet is the Kubernetes agent that is installed on every node. Kubelet is accountable for the precise execution of pods that are consigned to the node. Kubelet reveals a read-only API service that does not need authentication (TCP port 10255). Invaders with network access to the host (for instance, via running code on a compromised container) can send API requests to the Kubelet API. Specifically querying https://[NODE IP]:10255/pods/ retrieve the running pods on the node.
https://[NODE IP]:10255/spec/
retrieves information about the node itself, such as CPU and memory consumption.
https://[NODE IP]:10255/spec/
retrieves information about the node itself, such as CPU and memory consumption.
Network mapping
Attackers may try to map the cluster network to gain information on the running applications, including scanning for known vulnerabilities. By default, there is no restriction on pods communication in Kubernetes. Accordingly, attackers who gain access to a single container may use it to probe the network.
Access Kubernetes dashboard
The Kubernetes dashboard is a web-based UI that is utilised for monitoring and managing the Kubernetes cluster. The dashboard empowers users to perform actions in the cluster using its service account (Kubernetes-dashboard) with the permissions that are determined by the binding or cluster-binding for this service account. Attackers who gain access to a container in the cluster can utilise its network access to the dashboard pod. Consequently, attackers may retrieve information about the various resources in the cluster using the dashboard’s identity.
Instance Metadata API
Cloud providers provide instance metadata service for reclaiming information about the virtual machine, such as network configuration, disks, and SSH public keys. This service is available to the VMs via a non-routable IP address that can be accessed from within the VM only. Attackers who gain access to a container may query the metadata API service for acquiring information about the underlying node. For instance, in Azure, the following request would retrieve all the metadata information of an instance: http:///metadata/instance?api-version=2019-06-01


