Threats,Tactics and Procedures TTP
MITRE’s SHIELD® ACTIVE DEFENCE
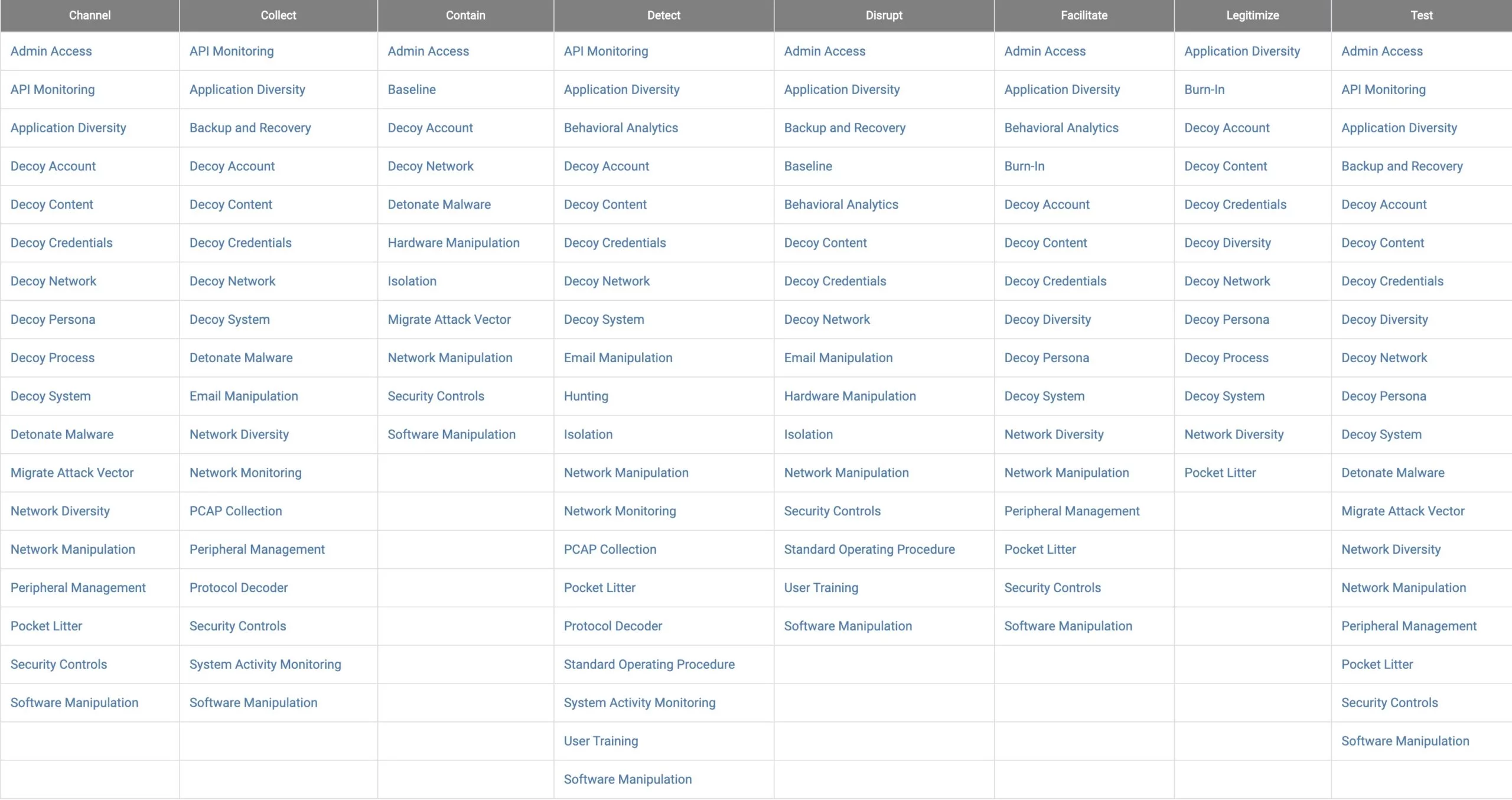
Channel
Channel is used to guide an adversary down a specific path or in a specific direction. A defender can channel an adversary away from important systems or network segments and towards decoy systems or hardened devices. They could also attempt to channel an adversary based on the content that you provide. Channelling can be used to waste an adversary's time, make them expend additional resources, or allow defenders to study their behaviours.
Collect
Gather adversary tools, observe tactics, and collect other raw intelligence about the adversary's activity.
Collect is used to gather information about an adversary or their activity that can inform other defences. It includes gathering logs that can be used to create detections. It also includes collecting malware samples that can be used for adversary engagement, hunting, or other purposes.
Collect is used to gather information about an adversary or their activity that can inform other defences. It includes gathering logs that can be used to create detections. It also includes collecting malware samples that can be used for adversary engagement, hunting, or other purposes.
Contain
Prevent an adversary from moving outside specific bounds or constraints.
Contain is used to prevent an adversary from moving outside specific bounds or constraints. This may include preventing them from accessing certain subnets or systems based on where they are operating. Defenders can also harden systems to prevent them from moving laterally.
Contain is used to prevent an adversary from moving outside specific bounds or constraints. This may include preventing them from accessing certain subnets or systems based on where they are operating. Defenders can also harden systems to prevent them from moving laterally.
Detect
Establish or maintain awareness into what an adversary is doing.
Detect is used to establish or maintain awareness into what an adversary is doing. This could be accomplished by introducing a tripwire that alerts when an adversary touches a system or resource. It could also be accomplished by using end-point or network tools.
Detect is used to establish or maintain awareness into what an adversary is doing. This could be accomplished by introducing a tripwire that alerts when an adversary touches a system or resource. It could also be accomplished by using end-point or network tools.
Disrupt
Prevent an adversary from conducting part or all of their mission.
Disrupt is used to prevent or discourage an adversary from conducting part or all of their mission. This may include increasing the time or skills needed to accomplish a specific task or by tightening controls so that more steps need to be taken.
Disrupt is used to prevent or discourage an adversary from conducting part or all of their mission. This may include increasing the time or skills needed to accomplish a specific task or by tightening controls so that more steps need to be taken.
Facilitate
Enable an adversary to conduct part or all of their mission.
Facilitate is used to enable an adversary to conduct part or all of their mission. This could include using unpatched versions of operating systems and software, removing end-point detection software, and using weak password. It may also include opening firewall ports, adding proxy capabilities, or introducing elements that an adversary can easily leverage to bypass an obstacle in their operations.
Facilitate is used to enable an adversary to conduct part or all of their mission. This could include using unpatched versions of operating systems and software, removing end-point detection software, and using weak password. It may also include opening firewall ports, adding proxy capabilities, or introducing elements that an adversary can easily leverage to bypass an obstacle in their operations.
Legitimise
Add authenticity to deceptive components to convince an adversary that something is real.
Legitimise is used to add authenticity to deceptive components to convince an adversary that something is real. This includes adding realistic user accounts, files, system activity, and any other content that an adversary might expect to see.
Legitimise is used to add authenticity to deceptive components to convince an adversary that something is real. This includes adding realistic user accounts, files, system activity, and any other content that an adversary might expect to see.
Test
Determine the interests, capabilities, or behaviours of an adversary.
Test is used to determine an adversary's interests, capabilities, behaviours, motivations, etc. This may include things like providing systems to see if an adversary engages or providing content to see if the adversary inspects or exfiltrates it. You can also test an adversary by making a tasks more difficult to perform and see if they have the capabilities to accomplish it.
Test is used to determine an adversary's interests, capabilities, behaviours, motivations, etc. This may include things like providing systems to see if an adversary engages or providing content to see if the adversary inspects or exfiltrates it. You can also test an adversary by making a tasks more difficult to perform and see if they have the capabilities to accomplish it.