Software-Defined Networking
SDN Pen Test
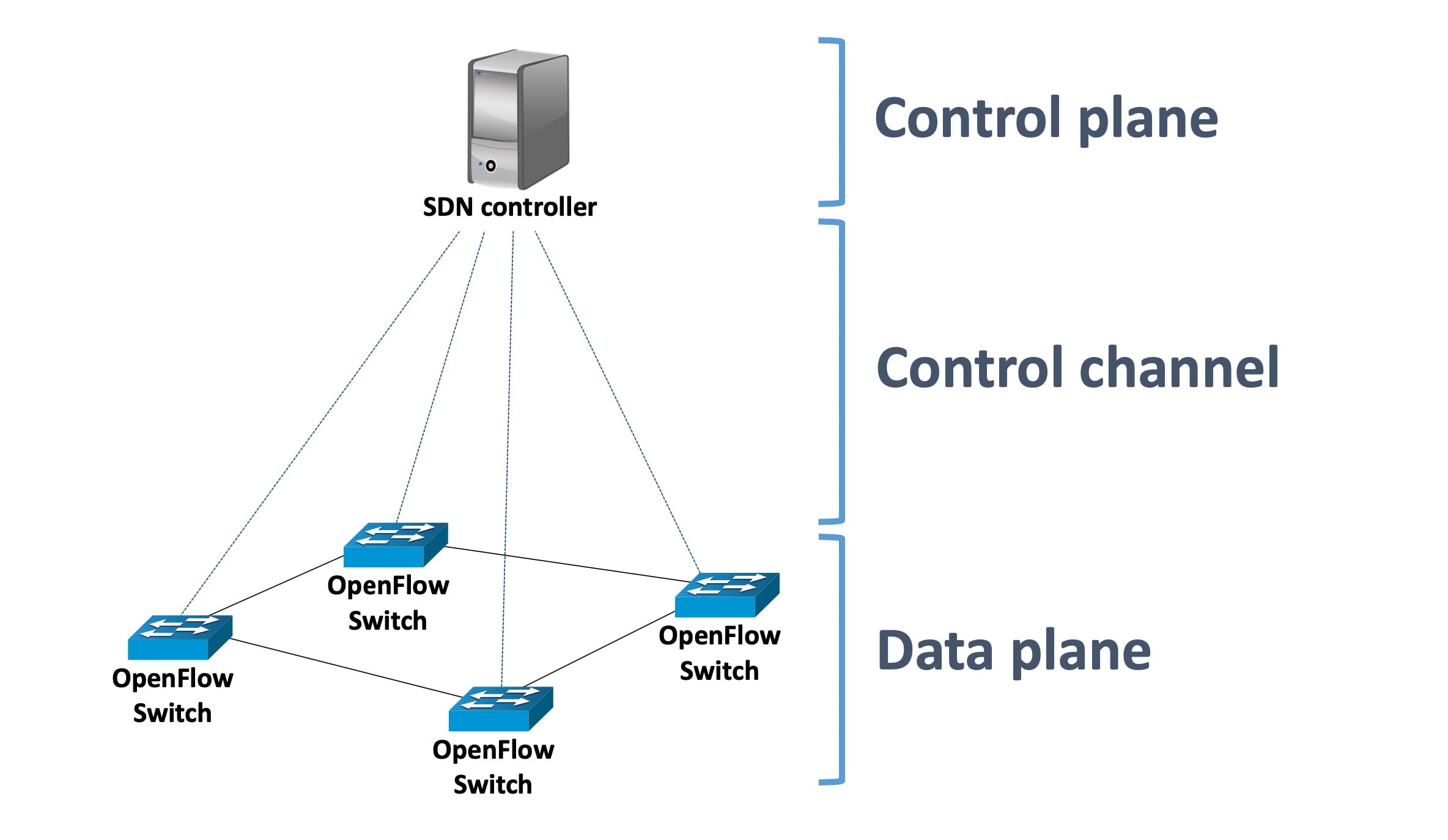
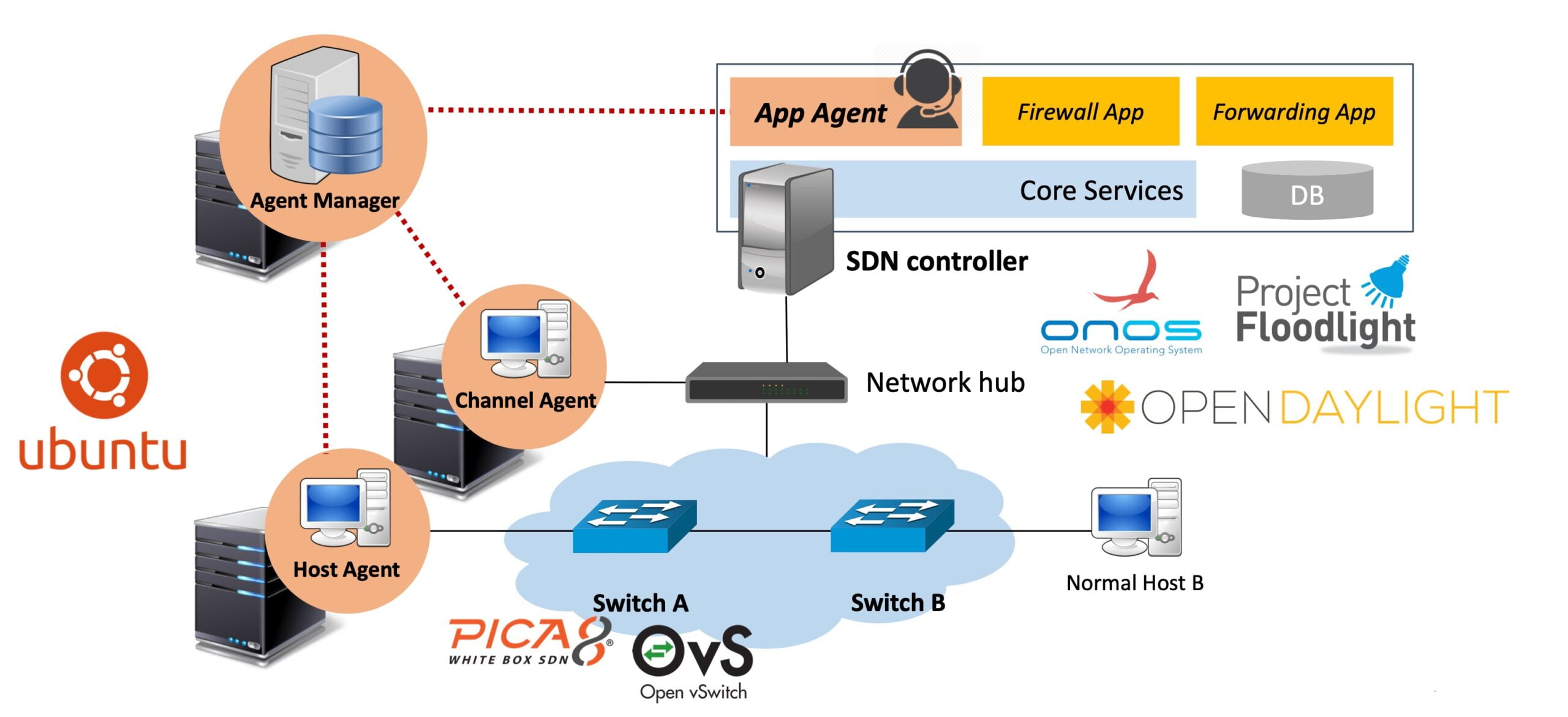
SDN PenTesting
roadmap
ARP Spoofing Attack
A Man-in-the-middle attack (MiTM) or ARP cache-poisoning. A malicious intruder uses an ARP spoofing to infiltrate the network, sniff packets, transform it and even halt it. It corrupts the network topology data and the topology-aware SDN apps. Protocols such as LLDP or IGMP are other attack-vectors
Traffic sniffing
A sniffing denunciation is a conventional technique used by the hacker to catch and examine network communication data. Eavesdrop data from network links and steal valuable information. Exploiting unencrypted communications to intercept traffic from and to a central controller. The data occupied could incorporate critical knowledge on flows or transport recognised on the network.


