A denial of service (DoS) attack is an attack that stops an authorised user from accessing the resource, either a server or a web app or network storage.
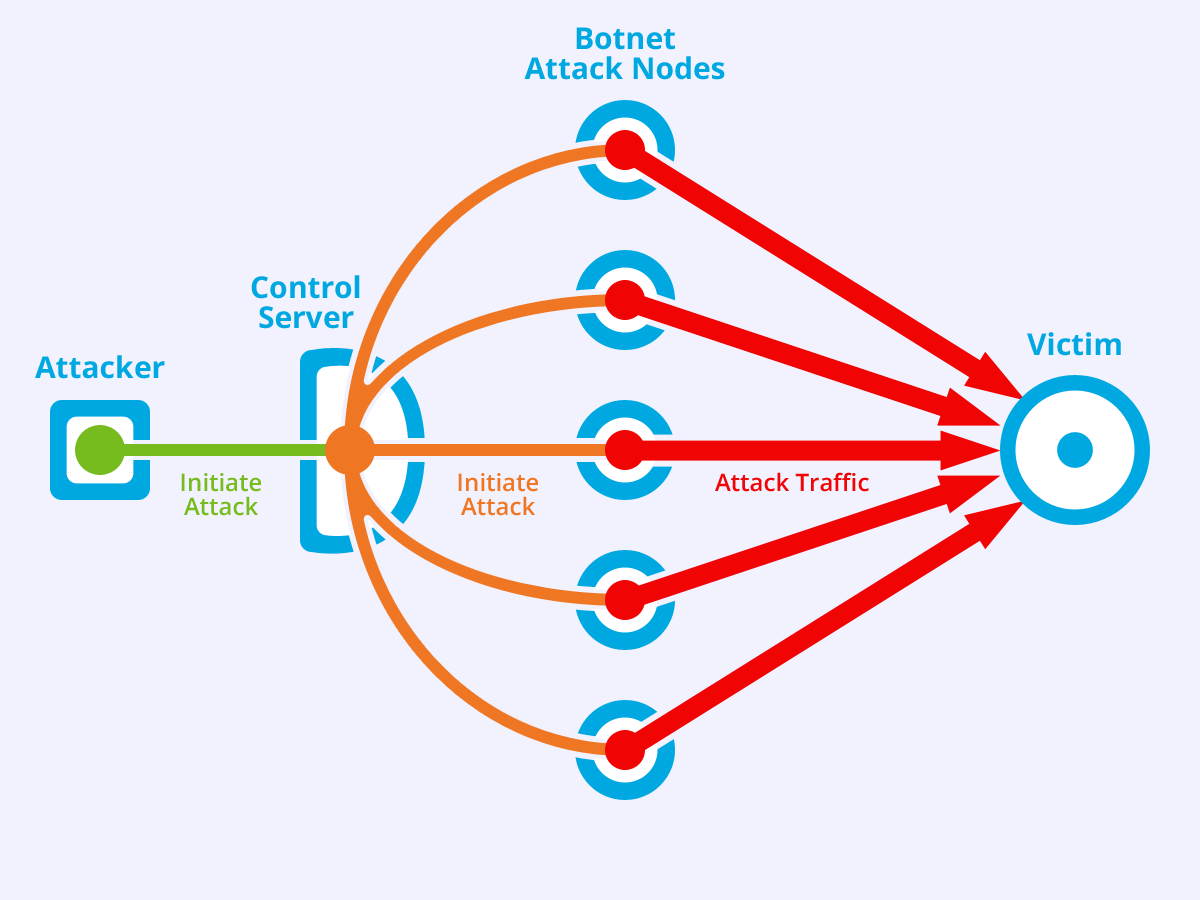
A distributed denial of service (DDoS) attack utilises numerous network resources as the origin of the precise adversarial vector.
DDoS is primarily a method to augment the capacities of an individual critic. Nevertheless, it may aid to cover the identity of an intruder and impede risk elimination attempts.
Most DDoS attacks leverage a “botnet”, that is a network of Internet-connected systems centrally managed by an intruder. Botnets may vary in capacity from a few techniques to hundreds of billions. Most botnets employ arbitrated network resources without the consciousness of the system owner.
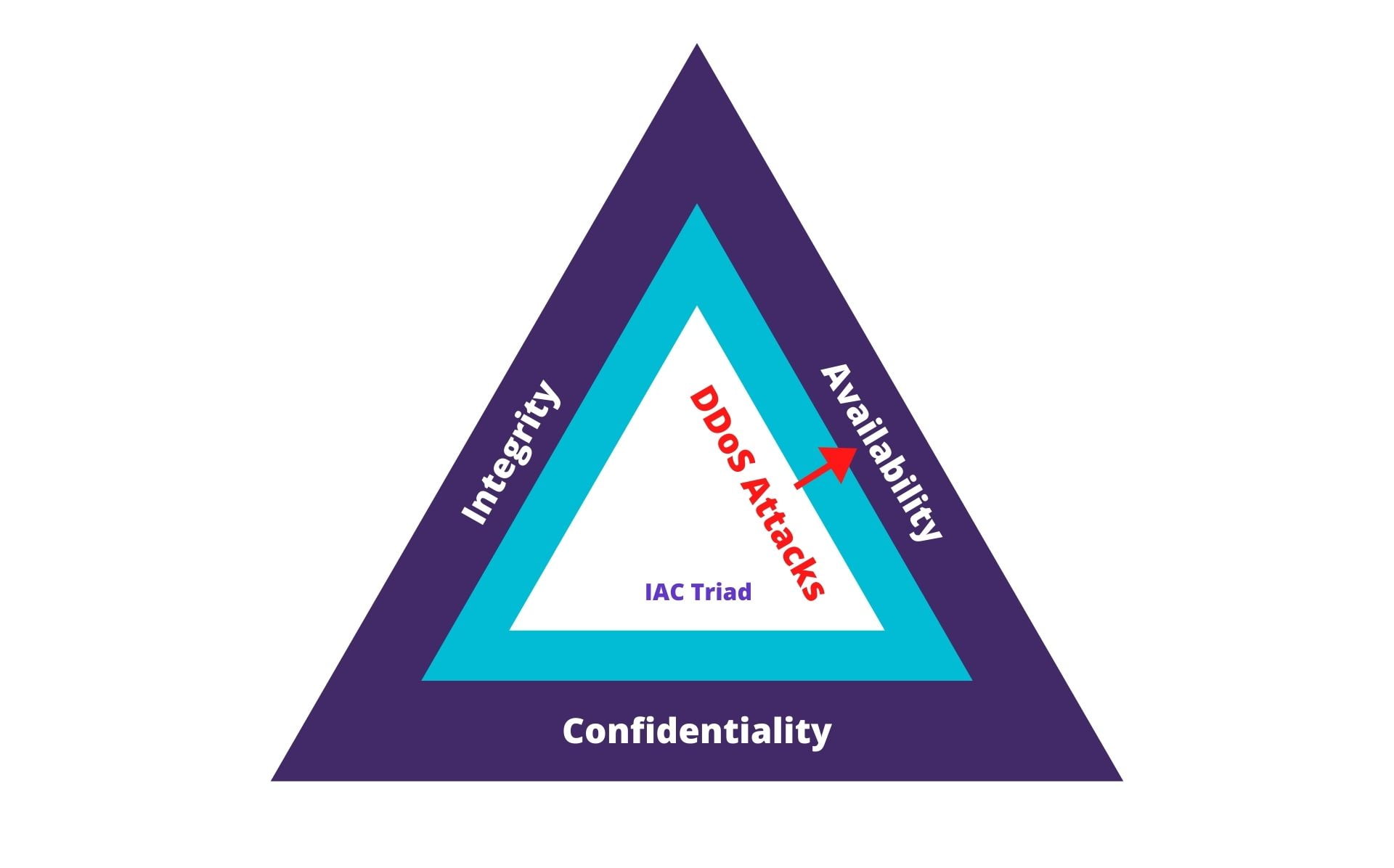
DDoS diverges from distinct areas of cybersecurity exploitation that endeavour to reconstruct or gain access to data to cause outages. DDoS intrusion signifies that the perception is the authorised user’s access to the data that contributes value for an organisation and excluding disrupts the business continuity.
Purpose
Websites are the keynotes of the business and a principal target for cybercriminals. Extensive networks of bots encompass to pursue disastrous Distributed Denial of Service (DDoS) attacks, braking down or disallowing admittance to resources (servers, websites or any apps) that lack precise security while serving as smokescreens for malware and exploits. The consequences may persist prolonged after the real attack is over. It results in a lack of trust of the clients, regulatory penalties, and plunging profits. Infrastructure demand to be shielded from DDoS attacks while assuring an optimal client experience at all eras. The challenge is to gain authentic users are not obstructed during an intrusion or constrained to complicated, disturbing problems similar to CAPTCHA protection to go to the website.
Consequences of the DDoS Attacks
Injury to Credibility
By causing an interruption, an intruder can negatively affect the status of a company.
Direct Revenue Damage
A blackout to a network means that undeviatingly generates income, such as E-commerce or online banking, can directly affect an organisation.
Dissipated Productivity
A DDoS attack often stops employees from completing their everyday responsibilities.
Attack Smokescreen
A DDoS attack conceals other treacherous movements from cybersecurity staff.
SNMP and SSDP remain the top sources for DDoS attacks, however nearly 800,000 WS-Discovery sources for exposed reflection amplification as well.
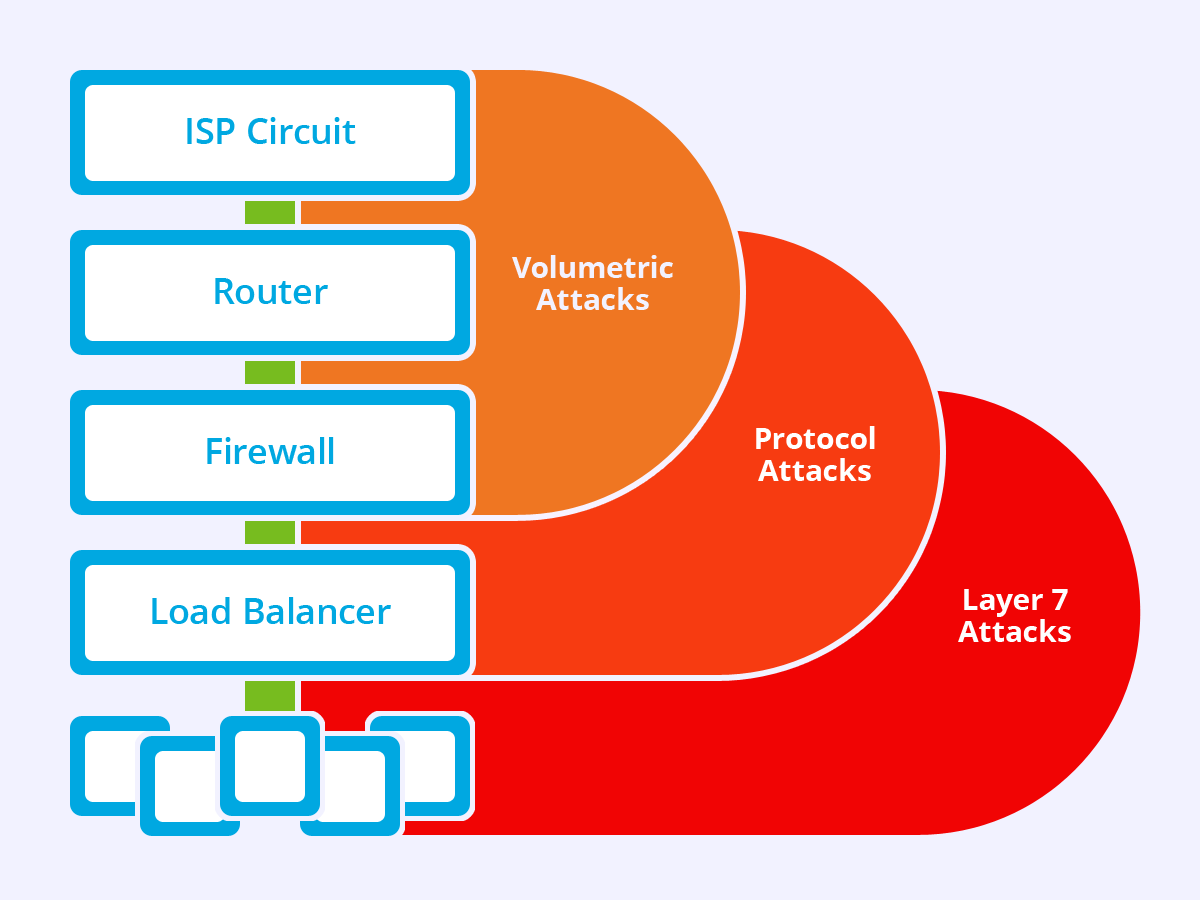
Volumetric DDoS Attacks
A volumetric DDoS attack is an attack that strives to overwhelm the victim by saturating the available system or network capacity. In simple terms, it uses all the available bandwidth of the entire network. And, all the relevant threshold allocated for the server/storage resources. It causes the Network Traffic jam, in other words.
Protocol DDoS
Attacks
Protocol adversaries consume up the processing volume of network infrastructures such as servers, unified communications storage (UCS), and load balancers by targeting Layer 3 and Layer 4 protocol interactions with malicious connection requests.
Application Layer DDoS Attacks
It is the further advanced DDoS attacks, and these exploit vulnerabilities in the application layer—Layer 7—by unfolding connections and inducting process and action requests that deplete finite resources like disk space and memory that is available.
Reflection And Amplification Attacks
Reflection and amplification attacks are a kind of volumetric DDoS attack where an intruder practices an intermediary system to enhance the size of an outbreak covering the exact origin of the intrusion.
benefits of
DDoS Pen Tests
- Mitigating botnet attacks
- Ensuring optimal performance of the content distribution
- Mitigate Extortion and minimise the risk of hacktivism.
- Build Cyber Resilience.
- Enhance Business Continuity.
- Prevent Disruption to the organisation’s revenues.
- Mitigate Personal Vendetta.
- Minimise Business Rivalry Risks.