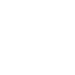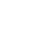Kubernetes is the most well-liked container orchestration system. Furthermore, one of the fastest-growing projects in the history of open-source enhances a significant part of many organisations’ compute stack. The versatility and scalability of containers inspire many developers to advance their workloads to Kubernetes. While Kubernetes has many benefits, it also brings new security challenges. Consequently, it is imperative to agree on the numerous security uncertainties that subsist in containerised environments, and especially in Kubernetes.
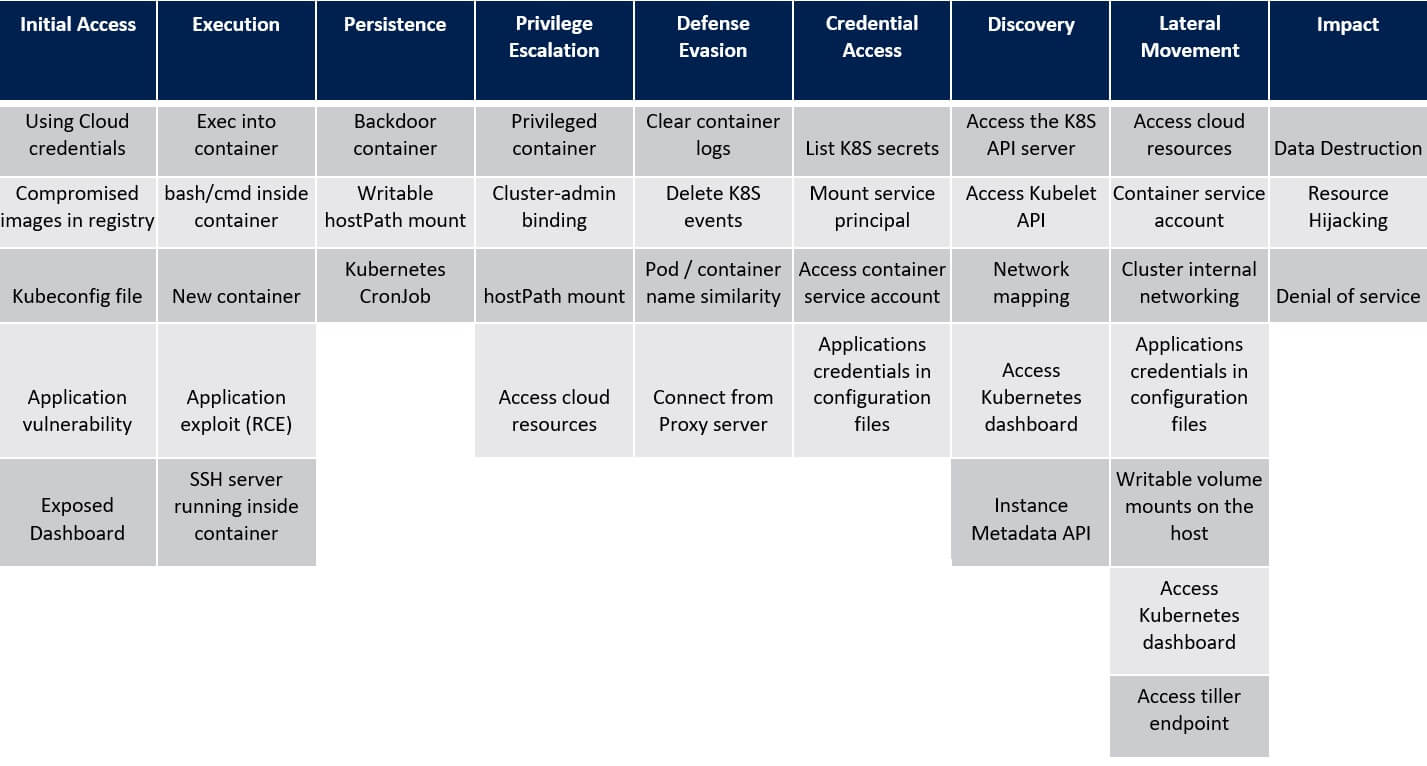
The MITRE ATT&CK® framework is a knowledge base of known tactics and techniques that are present in the cyberattacks. Begun with coverage for Windows and Linux, the matrices of MITRE ATT&CK comprise the multiple steps that are involved in cyberattacks (tactics) and refine the prized plans in each one of them (techniques). Those matrices aid organisations realise the attack surface in their environments and ensure they have sufficient detections and mitigations to the numerous risks.


MITRE ATT&CK framework tactics incorporate: