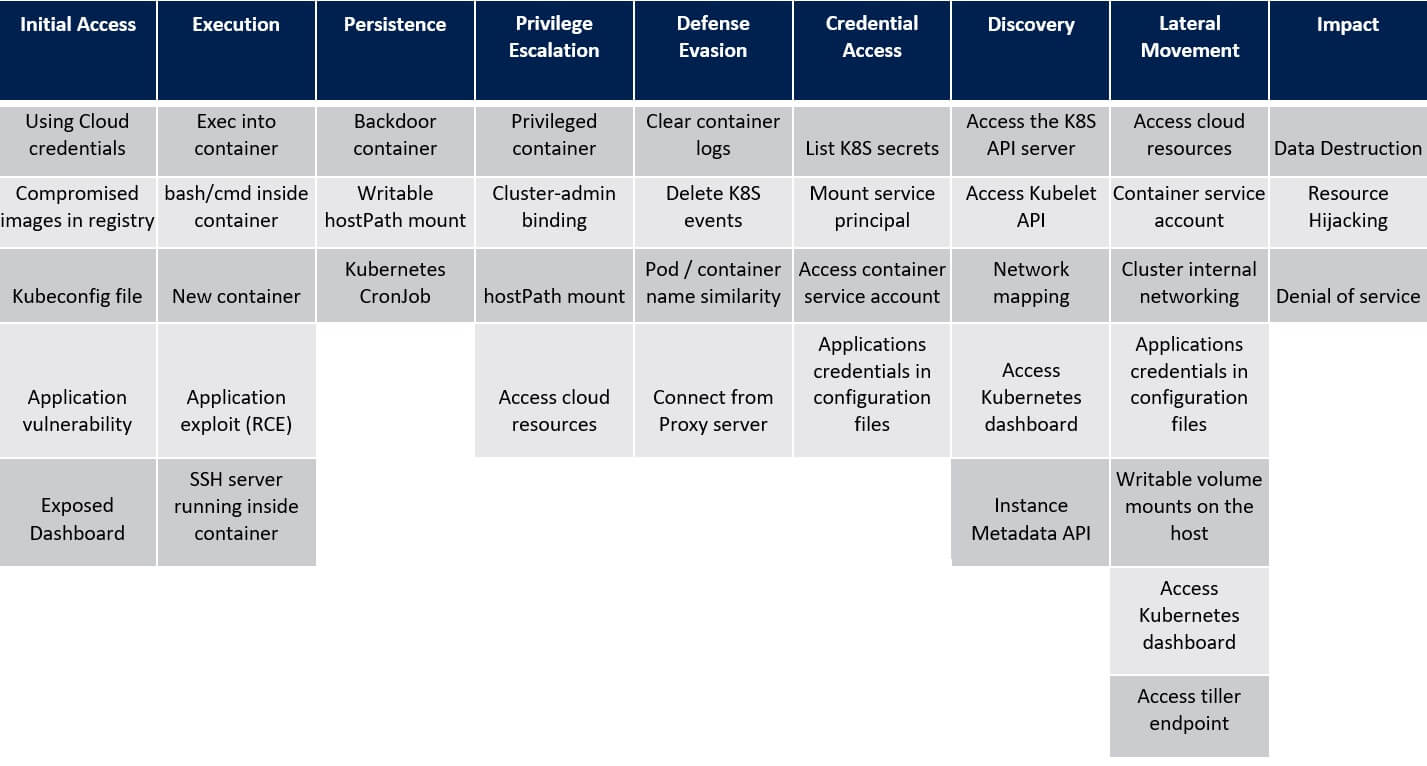
2. Malicious Execution on the Kubernetes Cluster – ATT&CK® Matrix
MITRE’s ATT&CK®
Application Exploit
After the application deployment in the cluster and if it is vulnerable to a remote code execution vulnerability, enables attackers to run code in the cluster. If the service account is mounted to the container (default behaviour in Kubernetes), the attacker will be able to send requests to the API server using this service account credentials.


