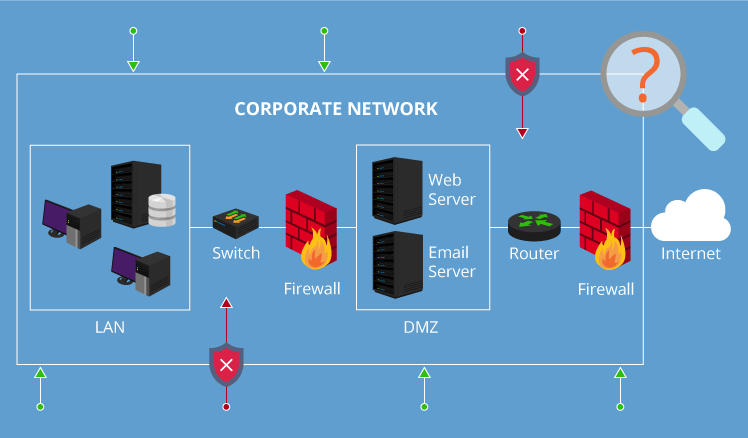
what is Vulnerability Assessment?
Analysing the Security gaps or Vulnerabilities in the entire infrastructure such as Servers, Networks, Websites and Mobile Apps and as well as Internet of Things (IoT).
Types
of Vulnerability Assessment
Phases of
Vulnerability Assessment
Automated Vulnerability Assessment – These are the steps usually performed in the traditional Vulnerability Assessment and is very time consuming.
Unauthenticated VA
Analyses the Vulnerabilities without login-credentials to discover the vulnerabilities.
Authenticated VA
Analyses the Vulnerabilities with login-credentials to validate the vulnerabilities.
FIND YOUR COMPANY’S
security gaps
Discover Vulnerabilities
Review Security Gaps
Review IT Security
Comply with GDPR norms and other Legal Regulatory and Compliance requirements.
Secure your Information.
Maintain Cyber Hygiene.