IoT is emerging technology–The Internet of Things.
• The Internet of Things (IoT) is the system of physical objects—devices, vehicles, homes and different things embedded with electronics, software, sensors, and network connectivity—that empowers these objects to gather and interact data
• Global 50+ billion appliances will be connected to the Internet by 2030
What is IoT penetration testing?
OMVAPT offers an impeccable penetration testing through our unparalleled offering of Attacker Simulated Exploitation for IoT.
It includes our security geeks arbitrating your system and devices with an adversarial mindset, thus unveiling any possible security loopholes that might lead to a security breach of your IoT device.
In most of the predicaments even though devices share similar kinds of vulnerabilities, we often dedicate our time into unprecedented forms of exploitation, and into things such as consolidating pair of minor critical vulnerabilities to succeed in a significant compromise.

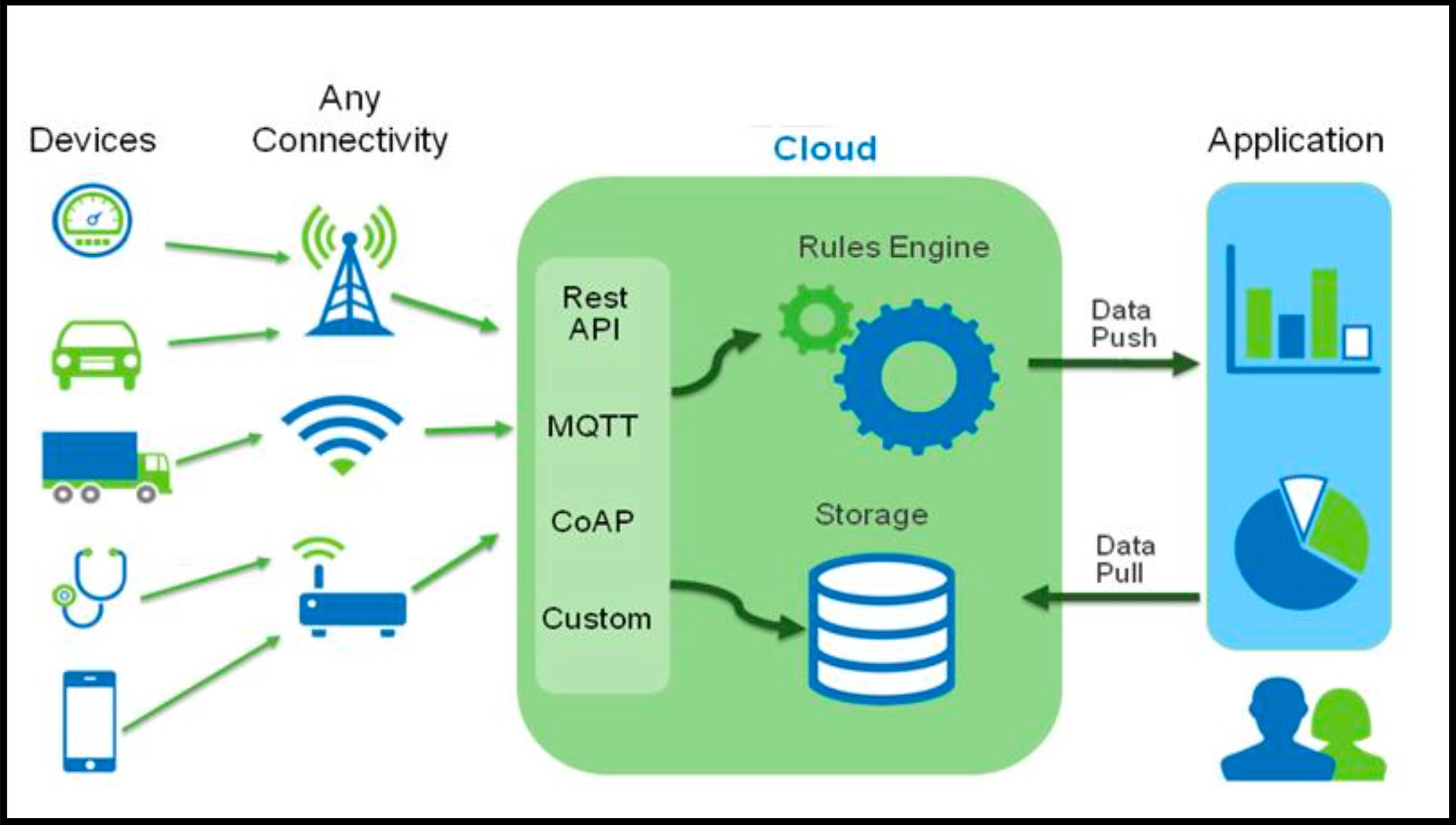
IoT Attack Methodology
Our entire team consumes among 3-4 days to perform an in-depth Attack Surface Plan of your IoT device.
We develop an extremely accurate architecture design highlighting all the feasible approach points for an ill-disposed dedicated intruder.
Reverse engineering the IoT firmware binaries
Encryption review and Obfuscation methods in use
3rd party libraries and SDKs
Binary reverse engineering and exploitation
Debugging binaries to obtain sensitive info
Evaluating hardware interface protocols such as UART, SPI, I2C etc.
JTAG debugging and exploitation
Logic sniffing and bus tampering
Dumping secret information and firmware
Proprietary information protocol reversing
Tampering security mechanisms
Glitching and Side-Channel attacks
Security hallmarks included in the hardware
Vulnerabilities in the web dashboard – OWASP Top – 10, OWASP Mobile Top 10, OWASP API Top 10, SANS Top 25
Mobile app security issues classification and exploitation for Android and iOS – Platform associated security issues, App was reversing, Binary instrumentation systems to gain sensitive data etc.
API based safety issues
Cloud-based and vulnerabilities in the backend operations
Analysis of radio communication protocols
Capturing the radio packets being sent and received
Modifying and replaying the packets for IoT device takeover attacks
Jamming based attacks
Obtaining the encryption key through numerous techniques
Radio communication reversing for proprietary protocols
Invading protocol-specific vulnerabilities
Exploiting IoT communication protocols such as BLE, ZigBee, 6LoWPAN, zWave, LoRa etc. through insecurities and vulnerable implementations
Ensuring that clients data storage is with the most leading standards.
Ensuring that there is no data loss such as PII through any courses – software, web, mobile, hardware or radio
Further assessment of data-at-rest and data-at-transit
Providing you with a PII report
An in-depth report comprising both technical aspects, non-technical review and an executive summary
Providing you with all the exploits and payloads, Proof of Concepts, exploitation procedures, demos or code fragments.
Categorizing the vulnerabilities based on criticality for your assigned product and user use-case synopsis
After patching the defects, we perform an in-depth reassessment to ensure there are no vulnerabilities.
We ensure that the patches did not inject any additional vulnerabilities as well.


