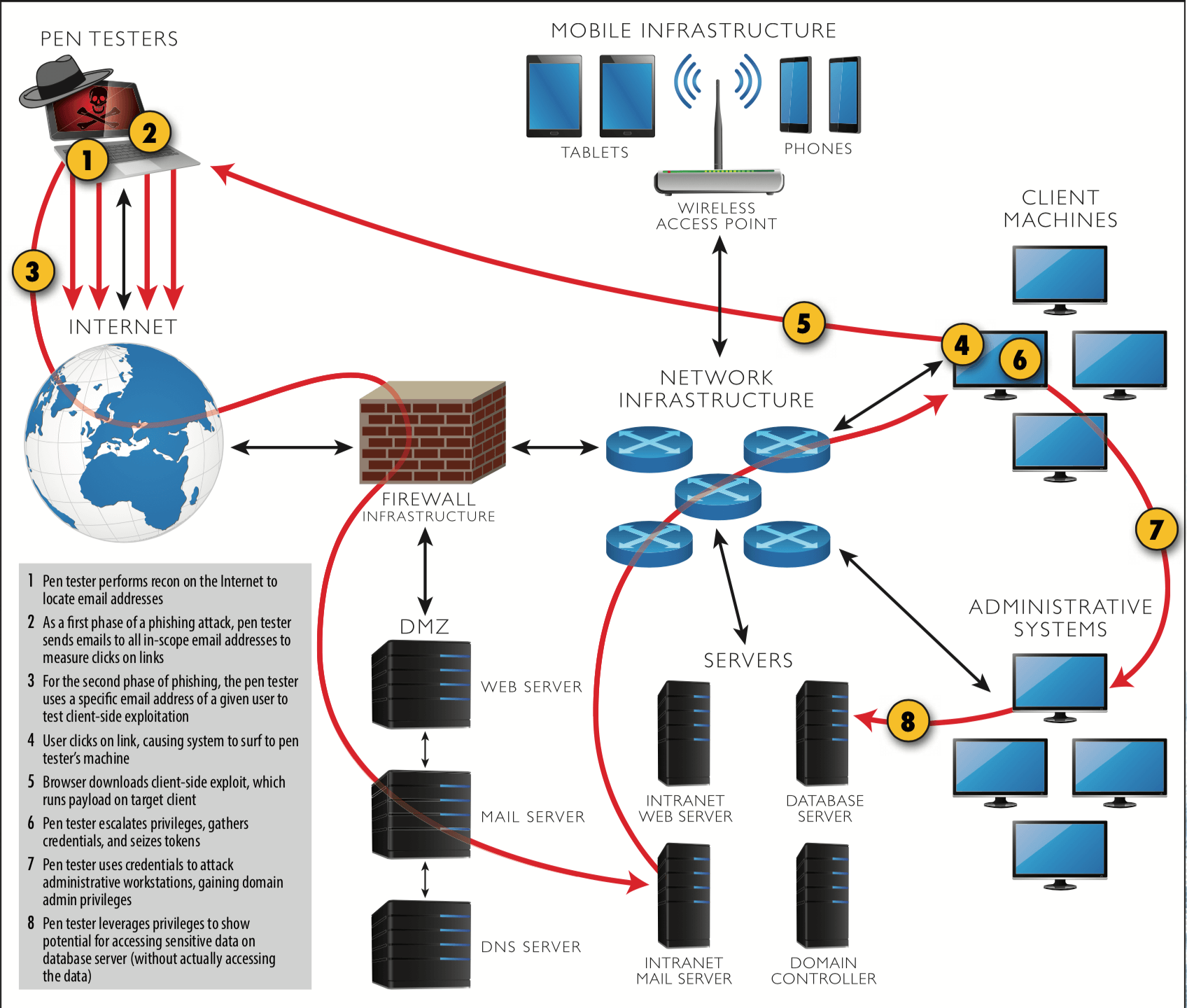
what is pen test?
Pivoting the found vulnerabilities by exploiting them to identify whether it is a genuine vulnerability (true- positive) or not (false-positive).PenTest simulates like that of an adversary with the intent to remediate and know the attack vectors of the adversaries.
Types
of Pen Test
External PenTest
Know the attacker’s intent from the external adversary’s views.
Internal PenTest
Know the attacker’s intent from the insider adversary’s views.
Phases of
PenTest
Penetration Testing (PT) or Ethical Hacking involves various phases and is very much similar to the military operation. The information collected in one phase will carry forward in another phase.
FIND YOUR COMPANY’S
attack vectors
Validate Vulnerabilities
Review Security Architecture
Attacker’s Intent
Comply with GDPR norms and other Legal Regulatory and Compliance requirements.
Enhance Brand’s Credibility.
Build Customer’s Trust.


