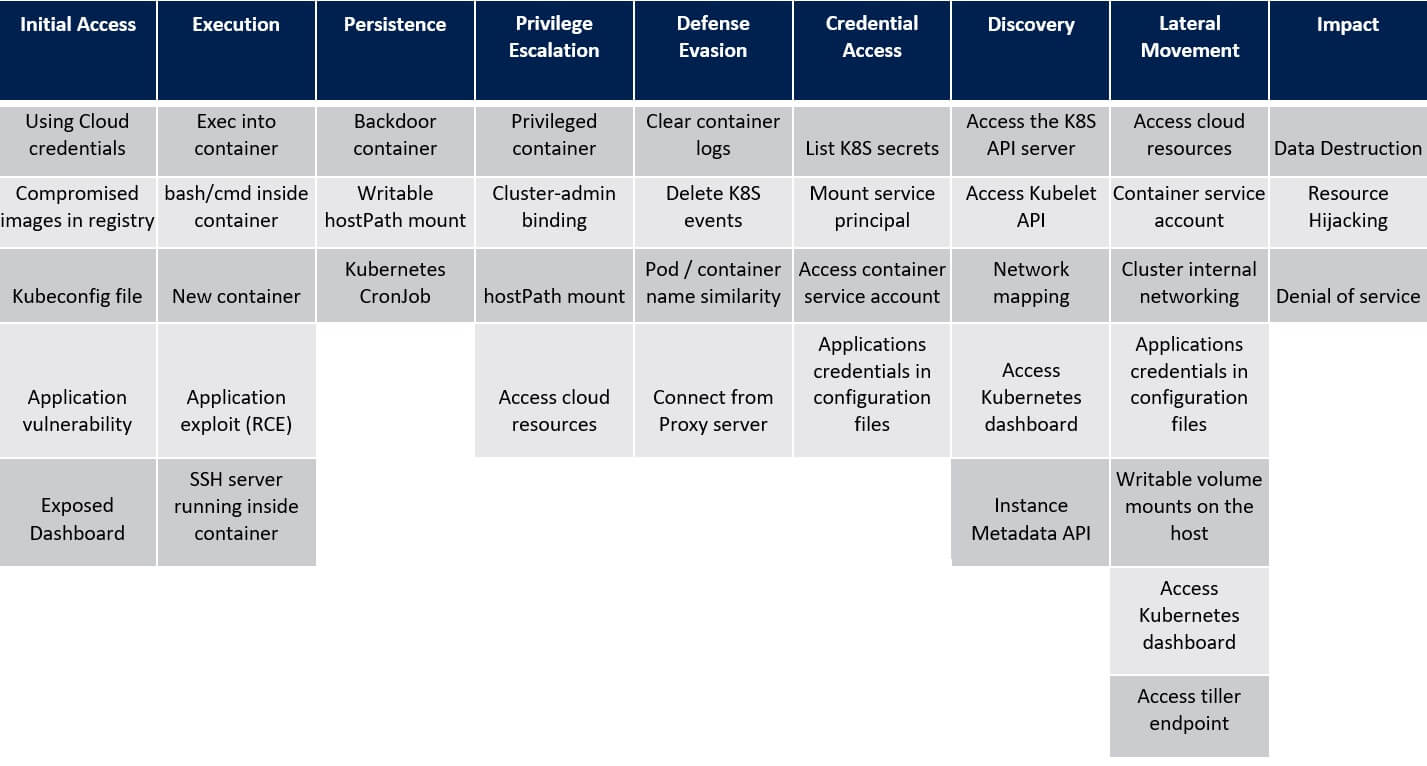
5. Defence Evasion – ATT&CK® Matrix
MITRE’s ATT&CK®
Delete K8S Events
A Kubernetes event is a Kubernetes object that logs state changes and failures of the resources in the cluster.
Example events are a container creation, an image pull, or a pod scheduling on a node.
Kubernetes events can be beneficial for recognising changes that happen in the cluster. Therefore, critics may want to delete these events (e.g., by using: “kubectl delete events–all”) in an attempt to evade detection of their action in the cluster.
Example events are a container creation, an image pull, or a pod scheduling on a node.
Kubernetes events can be beneficial for recognising changes that happen in the cluster. Therefore, critics may want to delete these events (e.g., by using: “kubectl delete events–all”) in an attempt to evade detection of their action in the cluster.
Pod or Container Name Similarity
Pods that are created by controllers such as Deployment or DaemonSet have a random suffix in their names. Attackers can use this fact and name their backdoor pods as the existing controllers created them. For example, an intruder could create a malicious pod named coredns-{random suffix} which would look related to the CoreDNS Deployment.
Also, attackers can deploy their containers in the kube-system namespace where the administrative containers reside.
Also, attackers can deploy their containers in the kube-system namespace where the administrative containers reside.


