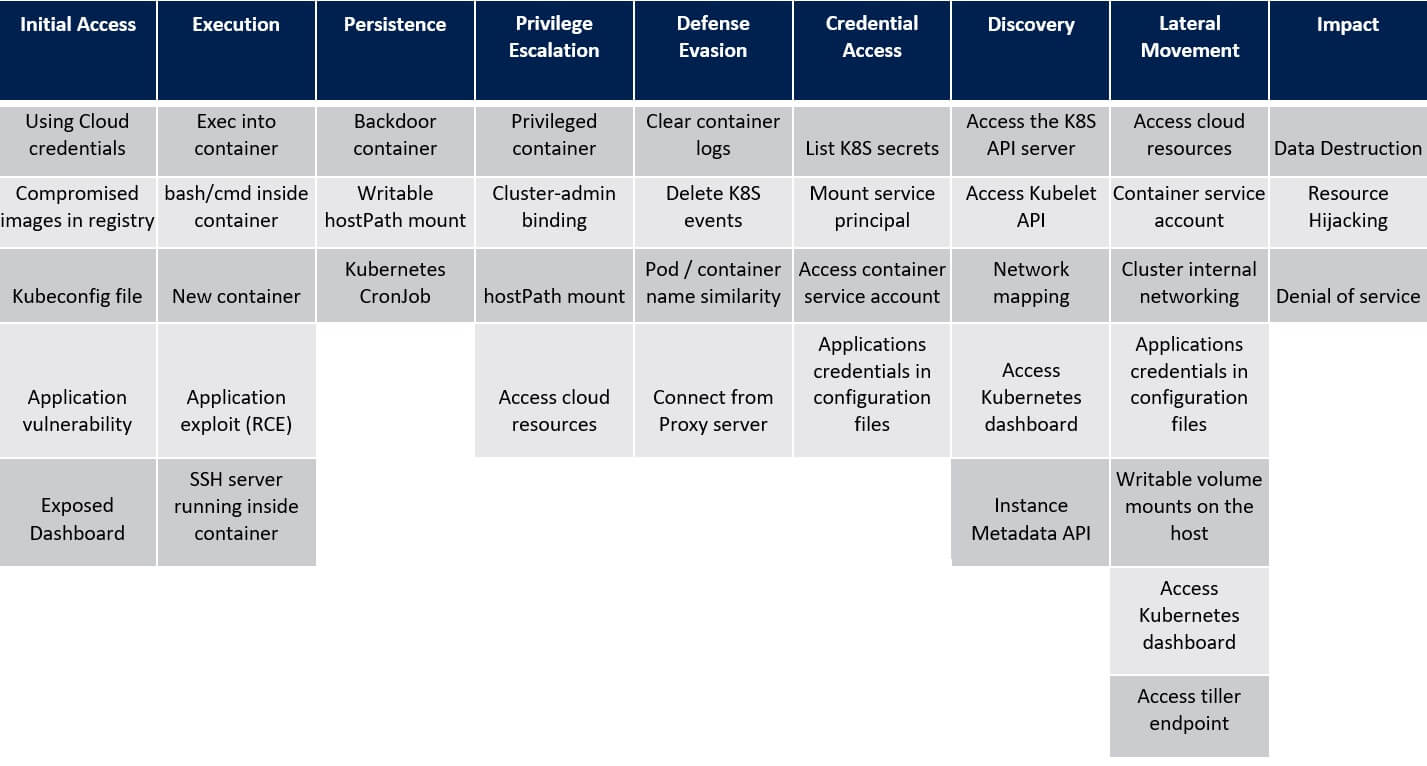
3. Persistence in the Kubernetes – ATT&CK® Matrix
Writable hostPath mount
hostPath volume mounts a directory or a file from the host to the container. Critics who have permissions to create a new container in the cluster may create one with a writable hostPath volume and gain persistence on the underlying host. For instance, the latter can be achieved by creating a cron job on the host.
Kubernetes Cronjob
Kubernetes Job is a controller that creates one or more pods and ensures that a specified number of them favourably terminate. Kubernetes Job may be used to run containers that perform restricted tasks for batch jobs. Kubernetes CronJob is used to schedule Jobs. Attackers may use Kubernetes CronJob for scheduling execution of malicious code that would run as a container in the cluster.