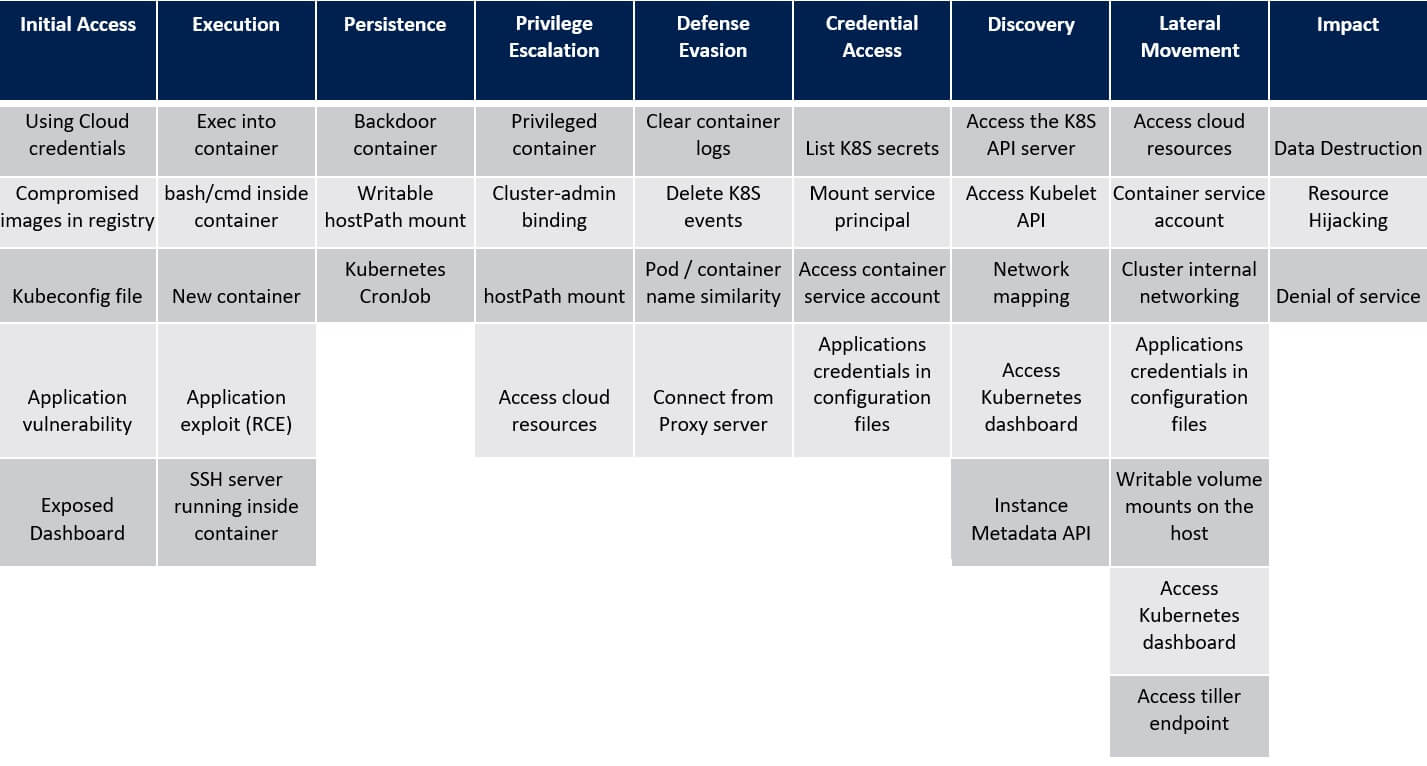
1. Initial Access to the Kubernetes Cluster – ATT&CK® Matrix
MITRE’s ATT&CK®
Cloud Credentials
The compromised cloud credential can direct to cluster takeover. It could lead access to the cluster’s management layer.
Example - Azure Kubernetes Service (AKS) in Microsoft Azure, Google Kubernetes Engine (GKP) in Google Cloud Platform (GCP), Elastic Kubernetes Service (EKS) in Amazon Web Services (AWS).
Example - Azure Kubernetes Service (AKS) in Microsoft Azure, Google Kubernetes Engine (GKP) in Google Cloud Platform (GCP), Elastic Kubernetes Service (EKS) in Amazon Web Services (AWS).
Compromised Images in Registry
Running a compromised image in a Kubernetes can arbitrate the entire cluster. Adversaries who gain access to a private registry can plant their arbitrary images in the container registry. Besides, users often use untrusted images from public registries (such as Docker Hub) that may be malicious.
Building images based on untrusted base images leads to similar results.
Building images based on untrusted base images leads to similar results.
Kubernetes Application Vulnerability
The public-facing vulnerable apps in a cluster enable primary foothold to the Kubernetes cluster. It could lead to Remote Code Execution and hence very well exploited. If the service account is mounted to the container which is the most default settings in the Kubernetes then requests can be sent to the API Server using the valid service account credentials.
Exposed Kubernetes Dashboard
The web-based user interface that enables monitoring and managing a Kubernetes cluster. By default, the dashboard exhibits an internal endpoint (ClusterIP service). If the dashboard is disclosed externally, it can allow unauthenticated remote administration of the cluster.


